By storing web page and resource copies web caches enhance browsing speed because users receive content faster than server fetches.
When hackers manipulate these stored content repositories into harmful capabilities the security risk increases.
This piece examines cache poisoning and explains its working mechanism and presents protection methods.
What is a Web Cache?
The procedure of storing temporary content through caching creates its copies. The web cache provides temporary storage for complete web pages alongside specific parts of web content while it remains valid for a designated period.
Web browsers maintain temporary storage of website elements which includes images and stylesheets and scripts. The site becomes faster at load time because your browser accesses saved data from cache storage rather than downloading everything anew.
The efficiency and user-friendly experience of browsing websites depend on caching because it reduces network data transfers which speeds up loading speeds.
TheCachedatacan resident at multiple areas such as:
When you browse the web your browser stores recent page and image along with other content copies for faster future visits.
The Content Delivery Networks known as CDNs maintain copies of web resources throughout several worldwide areas which ensure users access the closest server for quicker site performance.
The reverse proxy server functions as an intermediary between web server clients and users to store content that facilitates better server performance and faster response times.
Web caching operates according to several fundamental operational concepts as its basis.
CDN content has a temporal value called TTL which determines its expiration time. When a Time to Live (TTL) expires the cache content automatically becomes invalid.
A validation procedure enables the cache server to verify whether stored content needs updating or remains valid.
The cache deletion occurs as a website updates its content and this triggers the server to deliver the current version.
How Does Cache Poisoning Work?
A cyber-attack called cache poisoning enables hackers to modify web cache data storage by substituting it with an altered web page instead of genuine content.
Users who request cached content from the malicious server get altered data that might cause harmful scripts to activate in their browser software and put their security in danger.
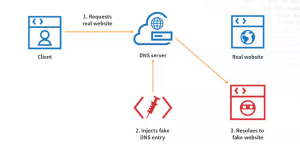
Hackers leverage the procedures that caching platforms use to store content in order to execute cache poisoning attacks. The following represents an easy-to-understand summary of the process.
The attacker conducts research to determine which website resources get stored in a cache system through their URLs or request headers.
Through their malicious request the attacker adds dangerous content that imitates legitimate content to enable the cache to store the response.
During the process the server provides a response after which the cache saves it. The malicious content continues to get stored by the cache server because it fails to execute proper request validation procedures.
Users who request saved resources receive an infected response instead of their original content.
Common Techniques Used in Cache Poisoning
Web caching mechanisms face several vulnerabilities which attackers use to execute cache poisoning attacks. Various common cache poisoning techniques consist of the following methods:
Attackers modify URLs and request parameters as they trick the cache server to store malicious content under legitimate requests.
Header Injection attacks trigger malicious header insertion into requests thus force the cache to accept and distribute dangerous content.
In Cookie Poisoning attackers modify request cookies to make the cache store and deliver material according to malicious session users.
Cache keys get manipulated by attackers to guarantee the storage and distribution of malicious content within the cache.
Attackers exploit cache setup errors through improper cache headers to establish functions that will allow them to serve harmful content.
How to Protect Against Cache Poisoning
We will now learn about protecting methods against cache poisoning attacks after understanding the attack mechanism.
Proper Input Validation
Every user input should undergo both validation and sanitization process while paying special attention to headers and parameters. The implemented protection ensures that attackers cannot add harmful content to the cached request information.
Use Secure Caching Headers
Set the correct “Cache-Control” together with “Expires” headers to stop sensitive data from being stored in the cache. Dynamic sensitive page content must use these caching headers: “no-cache,” “no-store,” and “must-revalidate.”
Control Cache Key Settings
Detective measures for cache keys should be configured correctly to prevent caching of responses containing user-specific parameters. Request headers along with query parameters should be configured in a way that makes them difficult to manipulate by attackers.
Implement HTTPS
HTTPS encryption protects data from attackers who try to modify or intercept both requests and responses between the web server and clients. Data integrity along with security measures combine to make cache poisoning attacks less likely through implementation of HTTPS.
You can find a beginner website development tutorial in my article Website Development Tutorial for Beginners Guide.
Conclusion
Web applications together with their users face substantial risk from cache poisoning because attackers exploit cached data to deliver harmful material while obtaining secret information.
You can safeguard your web applications from cache poisoning by studying its operation which must be combined with necessary security solutions. The correct protective measures will help you maintain user safety during online sessions.
You can continue read some of my blogs related development here.